The Importance of ACSC Essential 8 Compliance
The Australian Cyber Security Centre's (ACSC) Essential 8 framework provides organizations with a set of fundamental strategies to mitigate cyber threats and enhance their overall cybersecurity posture. Compliance with the Essential 8 framework is crucial for protecting sensitive data, preventing cyberattacks, and ensuring regulatory compliance. By implementing the recommended security controls, organizations can significantly reduce the risk of security breaches, minimize the impact of potential incidents, and safeguard their critical assets.
Understanding the Essential 8 Controls
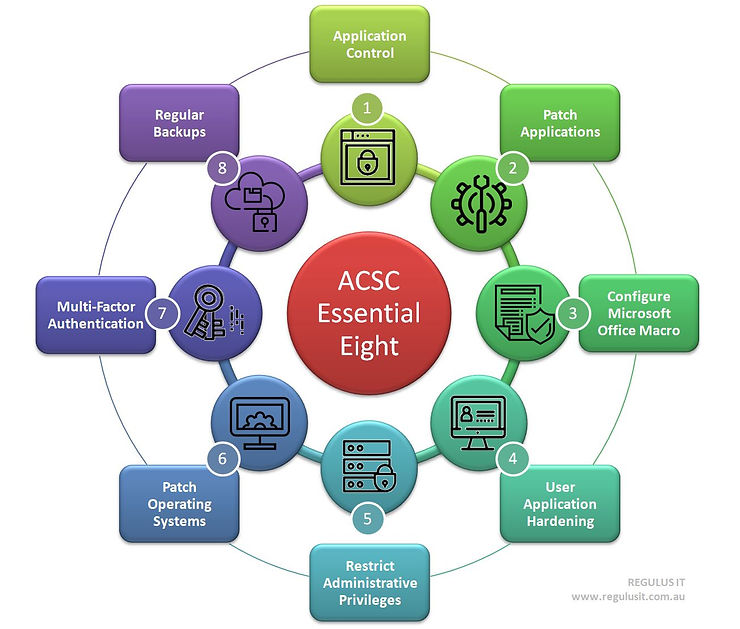
The Essential 8 framework comprises eight key security controls that organizations should implement to establish a strong defense against cyber threats. These controls include application whitelisting, patching applications, configuring Microsoft Office macro settings, user application hardening, restricting administrative privileges, patching operating systems, multi-factor authentication, and daily backups. Each control addresses a specific aspect of cybersecurity and, when implemented collectively, provides comprehensive protection against a wide range of threats.
Assessing Your Current Security Posture
Before embarking on the journey towards Essential 8 compliance, it is essential to assess your organization's current security posture. Conduct a comprehensive cybersecurity assessment to identify any existing vulnerabilities, gaps, or areas of improvement. This assessment will serve as a baseline for understanding the scope of work required to achieve compliance and guide the implementation process effectively.
Developing an Essential 8 Compliance Strategy
Creating a tailored compliance strategy is essential to ensure a systematic and efficient implementation of the Essential 8 controls. Start by prioritizing the controls based on risk and impact analysis, focusing on the most critical areas first. Develop a roadmap that outlines the necessary actions, resources, and timelines for each control's implementation. Engage relevant stakeholders, assign responsibilities, and establish clear communication channels to facilitate collaboration throughout the compliance journey.
Implementing the Essential 8 Controls
Implementing the Essential 8 controls requires a multi-faceted approach that combines technical measures, policy development, user awareness, and ongoing monitoring. Deploy robust security solutions, such as intrusion detection systems, firewalls, and antivirus software, to support the control implementation. Develop and enforce security policies and procedures that align with each control, ensuring consistent adherence and accountability. Conduct regular employee training and awareness programs to educate users about their role in maintaining compliance. Implement continuous monitoring and assessment mechanisms to identify and address emerging threats promptly.
Partnering with Compliance Experts
Achieving and maintaining compliance with the Essential 8 framework can be a complex and resource-intensive endeavor. Consider partnering with cybersecurity experts who specialize in Essential 8 compliance to ensure a smooth and effective implementation. These experts can provide guidance, conduct assessments, offer technical solutions, and assist with policy development, enabling your organization to navigate the compliance process efficiently while maximizing security effectiveness.
By prioritizing Essential 8 compliance, your organization can establish a robust cybersecurity foundation and proactively defend against evolving threats. Strengthen your defenses, protect sensitive data, and demonstrate a commitment to cybersecurity excellence by embracing the ACSC Essential 8 framework.
ACSC Essential Eight Cyber Security Framework